Many traders have locked positions in various wallets - that could be due to staking, holding specific tokens, or participating in certain smart contracts. Without the ability to import their private keys, traders would be forced to manage multiple wallets, complicating their asset management and paying for multiple solutions.
By supporting private key imports, Fordefi ensures that you maintain your positions and investments without having to unstake or move the funds. Moreover, supporting the import of a private key from another crypto wallet allows you to consolidate your assets into a single wallet solution or run another in parallel.
Using Fordefi's Import Key solution, you never need to reconstruct your key or run any scripts - you can upload the encrypted shares to Fordefi and decrypt the shares using the passphrase on your mobile device, keeping the integrity of the MPC protocol.
For your own security, Fordefi always recommends migrating from a different wallet provider by first generating a fresh set of keys in a new Fordefi workspace and then transferring assets that you have elsewhere, on-chain. This is preferred over moving your keys from your old wallet solution to Fordefi, which is an action that carries a higher risk.
Fordefi supports the import of private keys from two wallet types:
Fireblocks: You can migrate the existing wallets from your Fireblocks workspace into your Fordefi workspace by importing your Fireblocks key backup package.
Others (stand-alone): You can import a stand-alone private key that corresponds to a single wallet. For example, this could be the private key of a Metamask or Ledger wallet.
The import procedures for the two types differ slightly. See Dedicated Fordefi workspace.
The two types differ with respect to derivation:
Vault creation with imported Fireblocks keys requires key derivation. This also enables you to create multiple vaults that are all derived from the same master key.
In contrast, imported stand-alone keys do not support further derivation and each key corresponds to a single vault.
The import of existing keys requires a Fordefi workspace designated for key import. To tell if the workspace is suitable, click through to the Vaults screen and check that this banner appears:
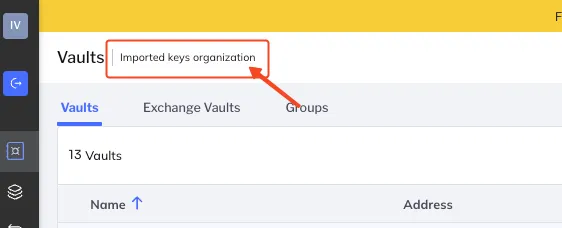
Contact Fordefi Customer Support to create such a workspace, if you require one.
The workspace has a set of native keys, like any other Fordefi workspace, but it also allows importing existing keys. The result is that in the workspace, there is one native set of keys and any number of imported keys.
To import keys successfully, you need:
An API User access token
Learn how to generate the token here.
A dedicated Fordefi workspace
(For Fireblocks private keys) Fireblocks recovery package items:
- Your
backup.zipfile - Your
RSA.pemkey - Your
RSA.pempassword (needed if you opted to password-protect your RSA.pem key) - Your Fireblocks recovery passphrase
If any of these items is missing, you'll need to obtain it from Fireblocks before starting the migration.
- Your
(For stand-alone private keys) Fordefi recovery tool
Download it from the Fordefi documentation site.
Note that you need the private key you want to import in hex format.
It is recommended that you back up all the keys in the workspace - both native and imported - as soon as you onboard the workspace. Keys that were imported into the workspace after creating the backup, will automatically be backed up as well. The advantage of including all keys in the backup is that it affords you a single, integrated, managed backup solution.
- While Fordefi, in general, supports ECDSA, EdDSA, ECDSA Stark and Schnorr key types, import of only ECDSA and EdDSA is currently supported. If you need support for keys of type ECDSA Stark or Schnorr, contact Fordefi Support.
- Fordefi does not show past transactions for imported vaults.