This page describes how to import private keys from a Fireblocks wallet.
It is recommended you learn more about performing this process and the prerequisites before you begin.
Repeat these steps for each key you wish to import.
Base64-encode your Fireblocks
backup.zipwith the following command:base64 -i ./fireblocks_backup_zip_file.zip -o base64_encoded_backup_zip_file.txtNow encrypt your RSA key with the following command. This command creates a secure, text-based representation of your encrypted RSA key that can be safely transmitted to Fordefi, who can then decrypt it using their corresponding private key:
openssl cms -encrypt -in YOUR_RSA_KEY.pem -recip cert.pem -aes256 -outform DER | base64 > base64_encoded_rsa_key.txtIn order to run this command successfully you'll need to download our
cert.pemand place it in the same folder where the command is being run. Please contact Fordefi support.Upload encrypted key material:
To start the import process, you will need to gather the relevant key material which can include the encrypted shares package and decryption key. You can either:
Contact support to initiate the import process.
ORCall the Import Keys API.
Here's a sample payload:{ "type": "fireblocks", "key_name": "<THE NAME OF THE KEY TO IMPORT>", "backup_zip_content": "<BASE64 ENCODED CONTENT OF YOUR BACKUP ZIP FILE>", "encrypted_rsa_pem": "<BASE64 ENCODED CONTENT OF YOUR BACKUP DECRYPTION KEY IN PEM FORMAT>", "rsa_pem_password": "<THE PASSWORD FOR THE BACKUP DECRYPTION KEY>" }You can upload the
encrypted_rsa_pemto be used to decrypt the enclave shares within thebackup_zip_content.Alternatively, you can use the following fixed public key to encrypt the shares, in which case you need to omit the
encrypted_rsa_pemandrsa_pem_passwordfields. The Fordefi enclave holds the corresponding private key.-----BEGIN PUBLIC KEY----- MIIBojANBgkqhkiG9w0BAQEFAAOCAY8AMIIBigKCAYEAxcYhWPOSYwV0zC1286Gd 2c7ptH/4atHqlRDxxsNr/1h3+F1EmjBXB0TdEiETHoEDvFrVTtkU2U9wwqxnFC1V NOWI3aOECgV93TaKeqvFQobB7xsfZ6Wi+dpTIMBSQGvxGI9RvVusdEF/1pveeYUt UDFl8/wZcvX74a2T3Kk02F4dt4JmH8hLD2XQhBhMdXFnYYGXaFLpzSovkCG0VHlz Y9j5YJH2Tvn2wlleCAoB+y/Nrbd6hHeUXLWJWgNwT06x8xJ6Nn6CBa37/aJbCPul F5lCQuD+zBHCPdVs3e6cakWA+bVinj/Ea/rfvQs1MuNdKxg6TRx/AVK77XRETJW2 R+F7ThJmBMI2g5y8wcY0zmnhNB6jsyI7Xd3AHCxkNgSajqTwg31AwJVDpo9KqbiD JT+njNOuRXHToIrZyU/sjO15XoX8j/6Q5i4UExiMOVE2b4shWg22Z9zMhSLpvwIr p3nCtTSVRqJySqBfwkjHdhNGZwSMGcEAAFRdvCUiJy5nAgMBAAE= -----END PUBLIC KEY-----
The response contains a set of keys, with an ID for each key. Here's a sample response:
{ "keys": [ { "key_id": "1e779c8a-6786-4c89-b7c3-a6666f5fd6b5", "key_name": "native-ecdsa", "key_type": "ecdsa_secp256k1", "key_origin": "native", "xpub": "xpub661MyMwAqRbcGE6Hjdqf5sQgNEAUAnghFLKBPQEGug3U1HG1sy4MLhEPLjUyyFfYvy45wMHQjAYEk7nHRznCwWSqi3WBQve7UWu1dXemXyv", "public_key_compressed": "A6YrN9ak58u3pOQHUossG2oFoVIPxvPP/b0fXkiMEJR8" } ] }Decrypt and run the MPC protocol:
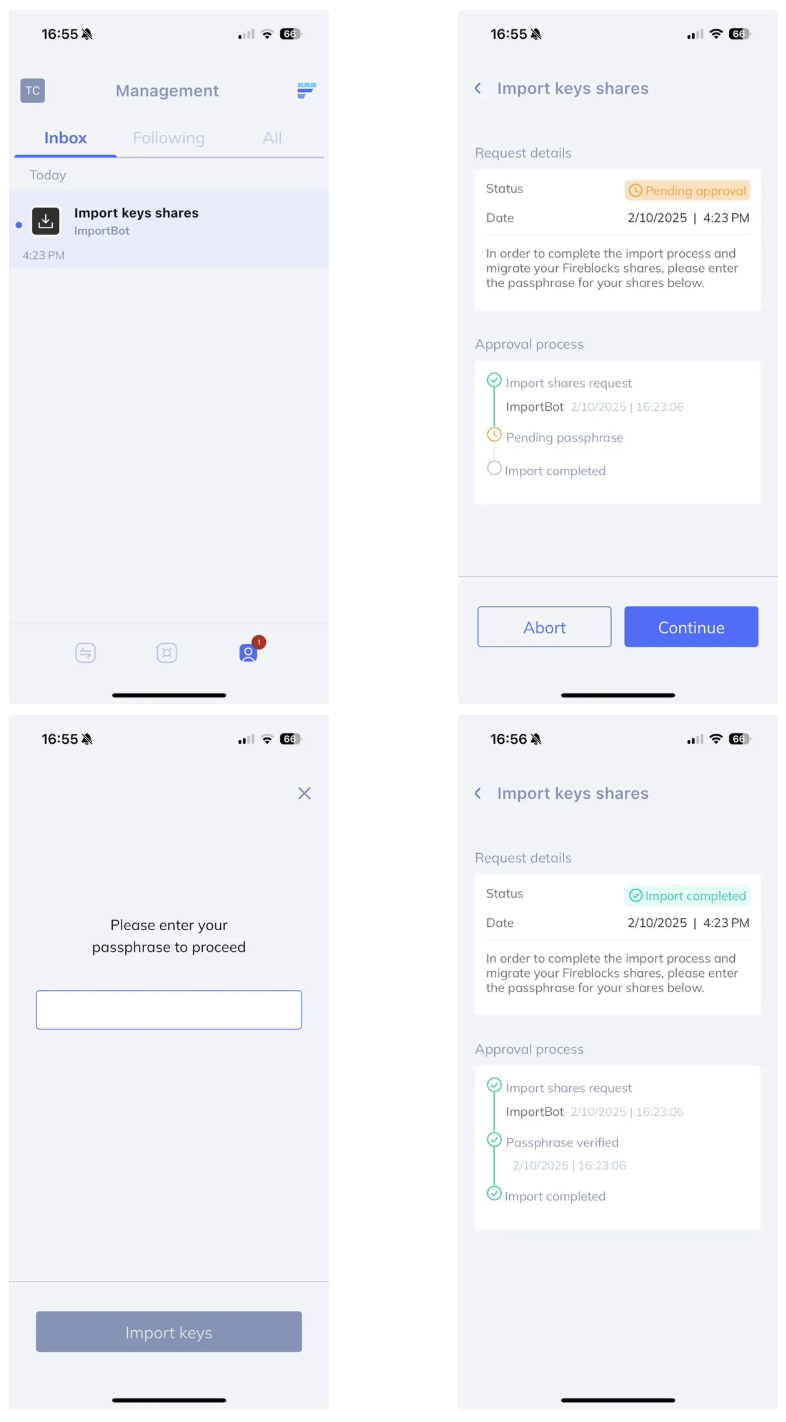
After you upload the key, all of the workspace's admins are notified. One of them must do the following: when prompted by the Fordefi mobile application, enter the Fireblocks recovery passphrase that will decrypt the mobile share.
Fordefi then loads the MPC shares into its secure enclaves and mobile device to be used in the platform.
You can now find the new key and its ID in the response to a call to the List Keys endpoint.
Continue to Create Imported Vaults.